i could easily eat you


hello
[KARA](https://ghost.computer) BECOMES DEVIANTI spent some time this week reading about twitter's bluesky project trying to understand why jack wants Twitter to be a client of a decentralized social media protocol.
At first I thought: Jack doesn't want to be responsible for speech, he wants to surf. He's banking on Twitter remaining the primary interface for most people and hoping the network will take care of moderation and he won't be phoned by senators anymore saying “why haven't u blocked alex jones yet”
But after reading one of the articles bluesky links to,
I think Jack wants the new protocol to be based on the blockchain. He likes bitcoin. So does Square, Inc. (https://twitter.com/jack/status/1108487911802966017).
This would help with his moderation problem, and his monetization problem. Interfaces earn bitcoin for having users, users earn bitcoin for retweets, that drives up the price of bitcoin and jack gets rich while he surfs.
Maybe it would be something less rainforest-burny like FileCoin or whatever. I'll bet Bitcoin is jack's preference, but it doesn't even matter if it's a brand new currency. jack would instantly have a huge amount of it, and its value would skyrocket.
I hope I don't think about it anymore this week.
I've been sick all week, and now Abe seems to have got whatever I've had. It's a really annoying fever-y thing.
Last night I had a dream where I was working on a garden with somebody from work. We were laying bricks and digging holes at the bottom of a residential hill. There were other people from work beside us working on different gardens. I looked up, there was an aeroplane flying overhead. It seemed to be hanging heavily to one side, and I saw steam or smoke escaping from areas other than the exhausts.
"is that okay?" i asked
"yeah, i think that's normal" said my colleage
"i really don't think that's OK," i thought (and didn't say)
Then the aeroplane swung dramatically to the right, up to the top of the hill. It was coming down at us very fast now, parts of it breaking off and nearly hitting folks who jumped out of the way at the last moment.
I looked over at my colleague, who was looking but didn't seem to have registered that we were going to die. Then I looked back at the aeroplane and woke up.
no reason to read into it
Last year me and Abe started working on some art together.
It's called today.

Each page has a picture made by Abe with Word '97 in a Windows 98 Virtual Machine, and a looping sound by me.

office '97 logo

old windows logo
I make the sounds with a Nintendo Game Boy, a handheld compact cassette recorder and a teenage engineering op-1.

a game boy with a cat face on the screen
teenage engineering op-1 cow fx. a black cow silhouette with flashing neon pipes
You can view the next sound/picture pair by clicking the picture, eventually you'll loop around.
The most recent one is on the homepage/.
There's an RSS feed you can subscribe to, and
you can append .json to any page (including the
root!) to get a JSON representation of that
page. Feel free to do whatever you want with that. The sounds and pictures are
all creative commons
share-alike.
Originally it was just a few HTML files, but when it started to take shape I wrote some scrappy JavaScript to generate the pages from a JSON file.
But that meant it was a manual process to put something live, or even preview a pairing.
So then I put together an app to manage the page. It takes uploaded media and puts it in Linode Object Storage (which is like S3 but without giving money to jeff).
There are three concepts. **sounds**, **pictures** and **days**.
The page for sounds shows a grid of every sound that isn't part of a day.
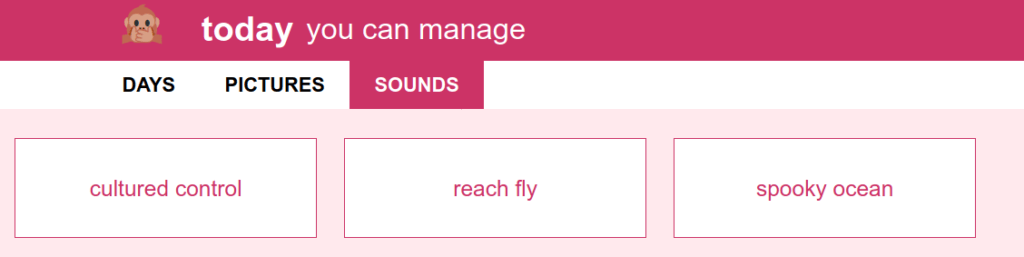
screenshot of the sounds page, showing three un-dayed sounds.
you can click one to preview it, and you can drag a .flac file onto the window
to upload a new one. It'll get a random name like spooky ocean. (adjectiveish noun).
The pictures page is a grid of all the pictures, paired or not.
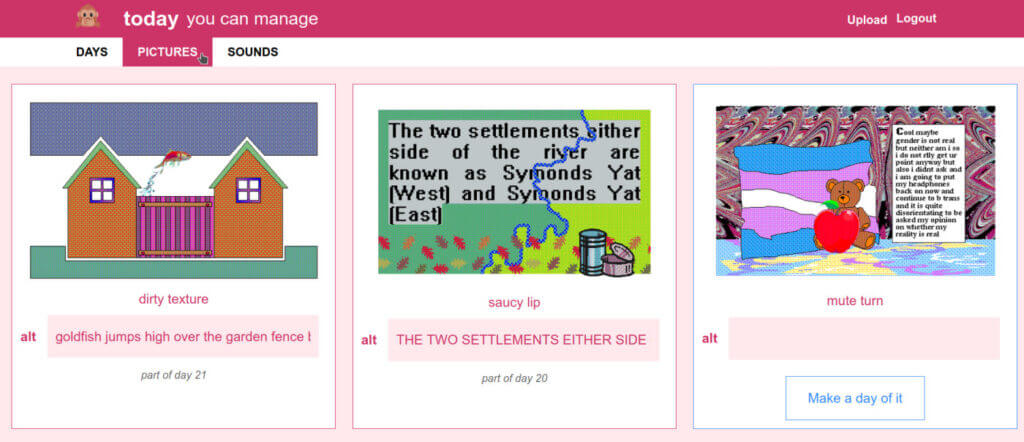
screenshot of the pictures page. two used and one unused picture.
This is where you add the alt text, and also where you can select the Make a day of it button.
The make a day of it page is where you can preview how a particular picture
will work with each available sound.
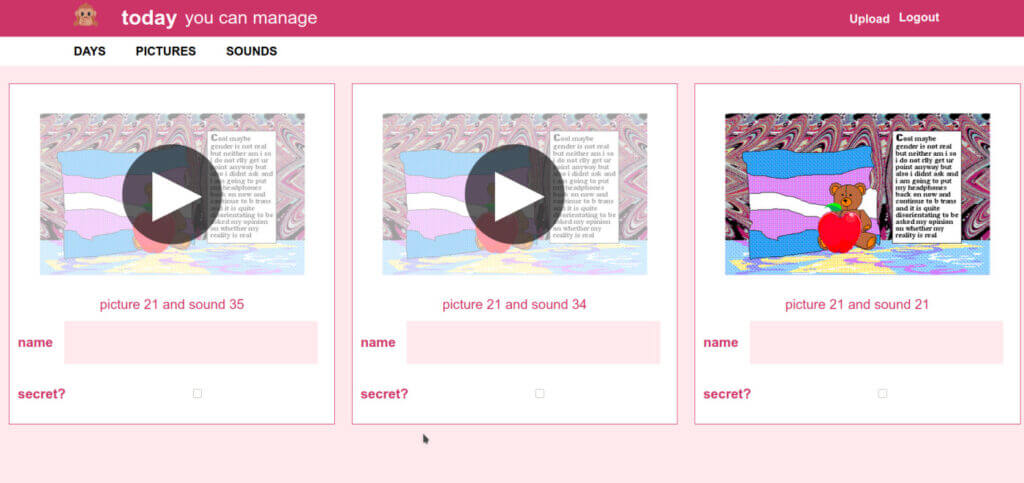
the “make a day of it” page
When you find something that works, you can give it a name and it will be the new homepage the very next moment.
The days page shows a grid of every day there's ever been.
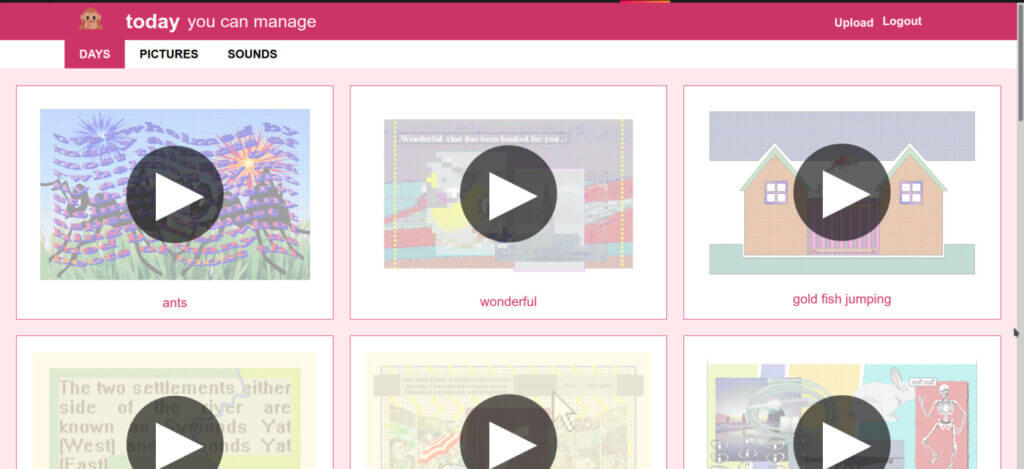
the homepage of today manager showing days
It's scary to have delete buttons lying around, so those are hidden behind
DANGER MODE, which can only be activated by manually adding ?danger=danger
to the URL.
After deleting anything, you're redirected back to the non-danger page.
ok, that's all. thanks.
password entry screen. it's the bad ending from bubble bobble.
⭐⭐⭐⭐⭐
=^.^=